Anti-spoofing is an essential technology for defending against cyber threats like IP spoofing, email phishing, and DNS attacks. This guide explains how anti-spoofing works, the different types of spoofing attacks, and the key methods for implementing spoofing protection.
Explore various techniques and software that help secure networks, emails, and data from attackers who impersonate trusted sources. By understanding and enabling anti-spoofing measures, businesses can better protect their sensitive information from potential cyber threats and vulnerabilities.
What is Anti-Spoofing?
Anti-spoofing is a defensive measure used in cybersecurity to prevent malicious actors from impersonating trusted entities, such as IP addresses, emails, or websites, to carry out cyberattacks.
These attacks, known as spoofing, can lead to data breaches, financial loss, or unauthorized access to systems. Anti-spoofing technologies and techniques work by validating the authenticity of data sources, detecting suspicious behavior, and blocking any malicious traffic before it can cause harm.
Commonly used anti-spoofing methods include packet filtering, email authentication protocols like SPF, DKIM, and DMARC, and security configurations for DNS and network traffic.
Types of Spoofing Attacks
Spoofing attacks come in many forms, each targeting different digital communication and security aspects. By impersonating trusted entities or manipulating data, attackers can gain unauthorized access, steal sensitive information, or disrupt services. Understanding the various types of spoofing attacks is crucial for implementing the right defenses.
Below are some of the most common spoofing methods that threaten network, email, and biometric security.
IP Spoofing
In IP spoofing, attackers manipulate the source IP address in data packets to disguise their identity. By making it appear as if the traffic originates from a trusted source, they can bypass security measures, launch Distributed Denial-of-Service (DDoS) attacks, or gain unauthorized access to systems.
Techniques
- Packet crafting to alter source IP addresses.
- Man-in-the-middle attacks using IP address forgery.
- Using botnets to perform Distributed Denial-of-Service (DDoS) attacks.
Software
- Wireshark: Used for network analysis and detecting spoofed IP packets.
- Snort: An open-source intrusion detection system that can be configured to identify IP spoofing attempts.
- TCPdump: A packet analyzer that helps detect anomalies in network traffic.
Email Spoofing
Email spoofing involves sending emails with a forged sender address, tricking the recipient into thinking the message is from a legitimate source. This type of attack is often used in phishing schemes to steal sensitive information or spread malware.
Techniques
- Faking sender email addresses using open mail relays or compromised email servers.
- Using phishing emails to trick recipients into clicking malicious links or providing sensitive information.
Software
- SPF, DKIM, and DMARC: Email authentication protocols to prevent email spoofing.
- Mimecast: Provides anti-spoofing and email security features.
- Barracuda Email Security Gateway: Detects and blocks email spoofing attempts.
Website spoofing
Website spoofing occurs when attackers create fraudulent websites that closely mimic legitimate ones. Users are tricked into entering sensitive information, such as passwords or payment details, which is then captured by the attacker. This type of attack is commonly used in phishing campaigns.
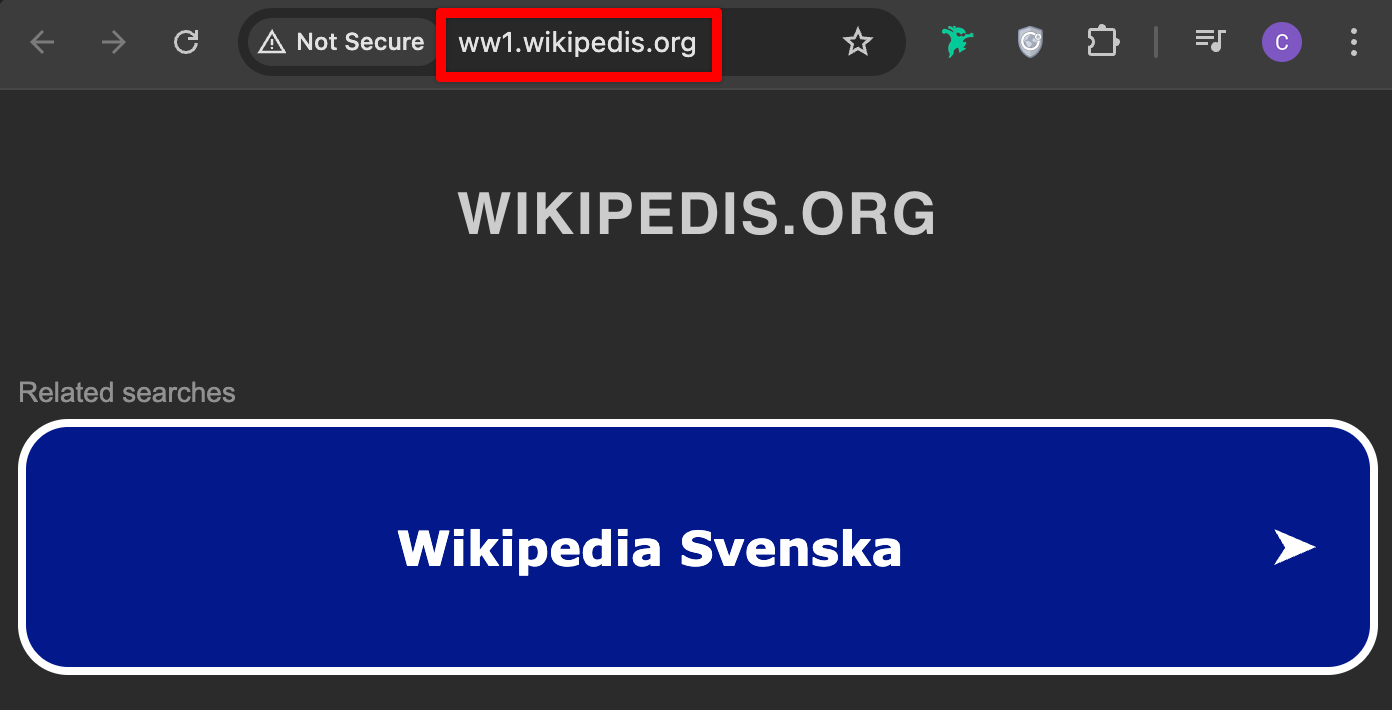
Techniques
- DNS poisoning or hijacking to redirect users to fraudulent sites.
- Using SSL certificates to make the spoofed website appear legitimate.
Software
- SSL/TLS validation tools: Ensure the authenticity of a website’s certificate to detect fake sites.
- SiteLock: Scans for website spoofing attempts and provides protection.
- Cloudflare: Protects against DNS-based attacks and ensures secure website communication.
Data replay attacks
In data replay attacks, attackers capture and retransmit data packets in a network, hoping to exploit security vulnerabilities. Even though the data packets are legitimate, the timing and intent behind their retransmission can lead to unauthorized access or manipulation of data.
Techniques
- Capturing data packets in transit and replaying them to trick the receiving system.
- Exploiting weak session tokens or authentication mechanisms.
Software
- Wireshark: For analyzing network traffic and detecting replayed packets.
- Burp Suite: Detects vulnerabilities that enable replay attacks in web applications.
Authentication replay attacks
Authentication replay attacks occur when an attacker intercepts authentication credentials and replays them to gain unauthorized access to a system or network. For example, an attacker may intercept a login token and use it to impersonate a legitimate user, bypassing security mechanisms.
Techniques
- Capturing login credentials during transmission and replaying them to bypass authentication.
- Exploiting weaknesses in systems that don’t use nonces or timestamps.
Software
- OpenSSL: Secures communications by encrypting data, preventing attackers from capturing authentication tokens.
- OAuth-based tools: Ensure secure token-based authentication to minimize replay attacks.
DNS Spoofing
DNS spoofing, or DNS cache poisoning, involves altering DNS records to redirect users to malicious websites instead of legitimate ones. This attack can lead to the exposure of sensitive data or the downloading of malware from fraudulent sites, all without the user realizing they’ve been redirected.
Techniques
- DNS cache poisoning to inject false DNS entries into a server.
- Man-in-the-middle attacks to intercept and alter DNS queries.
Software
- DNSSEC (Domain Name System Security Extensions): Protects against DNS spoofing by validating DNS responses.
- Pi-hole: A network-wide ad blocker that helps block DNS spoofing attempts.
- Unbound: A DNS resolver supporting DNSSEC to prevent spoofing.
ARP Spoofing
In ARP spoofing, attackers send false ARP messages within a local area network (LAN), associating their MAC address with the IP address of a legitimate device. This allows the attacker to intercept, modify, or block traffic intended for that device, often leading to man-in-the-middle attacks.
Techniques
- Poisoning the ARP cache of devices on the same local network.
- Intercepting or altering network communications in a man-in-the-middle attack.
Software
- Arpwatch: Monitors ARP traffic and detects suspicious ARP activity.
- Ettercap: Detects and prevents ARP spoofing and man-in-the-middle attacks.
- NetCut: Detects and prevents ARP spoofing activities within local networks.
Biometric spoofing

Biometric spoofing involves tricking biometric authentication systems, such as facial recognition or fingerprint scanning, by presenting fake or manipulated biometric data. Attackers might use photos, videos, or synthetic fingerprints to bypass security and gain unauthorized access.
Techniques
Presenting 2D images or synthetic fingerprints to bypass facial or fingerprint recognition.
Using 3D-printed masks to defeat facial recognition systems.
Software
- Liveness detection software: Detects real-life indicators, like blinking, to verify biometric inputs.
- FaceTec: Provides biometric anti-spoofing for face recognition systems.
- Precise Biometrics: Offers anti-spoofing solutions for fingerprint recognition.
Frame spoofing
Frame spoofing occurs when an attacker injects false information into communication frames within a network, such as wireless networks. By sending fake control frames, the attacker can disrupt network operations, redirect traffic, or impersonate legitimate devices.
Techniques
Crafting and injecting false frames into a wireless network to disrupt connections or impersonate legitimate devices.
Exploiting weaknesses in frame transmission protocols to take control of communications.
Software
- Wireshark: Analyzes network traffic to detect irregularities in frame sequences.
- Aircrack-ng: A suite for monitoring and detecting spoofing activities in wireless networks.
- Kismet: Detects and alerts administrators about frame spoofing attacks in wireless networks.
How Anti-Spoofing Technology Works
Anti-spoofing technology is designed to detect and prevent spoofing attempts across various communication channels, including emails, networks, and biometric systems. By validating the authenticity of data and verifying the source of communications, these technologies help prevent malicious actors from impersonating trusted sources. Below are two key components of how anti-spoofing technology works.
Email authentication mechanisms
E-mail authentication mechanisms are essential in preventing email spoofing attacks. They work by verifying that the sender of an email is who they claim to be, reducing the risk of phishing and other email-based attacks. Common email authentication protocols include:
- SPF (Sender Policy Framework)
- DKIM (DomainKeys Identified Mail)
- DMARC (Domain-based Message Authentication, Reporting, and Conformance)
Anti-spoofing software solutions
Anti-spoofing software solutions are tools designed to detect and block spoofing attempts across networks and communication systems. These solutions can monitor traffic, validate packet sources, and prevent the manipulation of IP addresses, DNS queries, or biometric data. Key features of anti-spoofing software include:
- Packet Filtering: Analyzes network traffic to identify and block suspicious data packets that appear to originate from spoofed IP addresses.
- DNS Security Tools: Protect against DNS spoofing by verifying the authenticity of DNS requests and responses.
- Biometric Anti-Spoofing Systems: Utilize advanced algorithms to detect fake biometric data, such as spoofed fingerprints or facial recognition, ensuring that only legitimate users can access secure systems.

Image Data Collection for Biometric System
- Biometrics, Facial Identification
- 2,000 photographs across 50 unique sets
- 1 month
Why Is Spoofing Protection Important?
Spoofing protection is essential for maintaining the security and integrity of digital communications, networks, and sensitive data. Without effective protection measures, businesses and individuals are vulnerable to a range of cyberattacks that can have serious consequences. Here’s why spoofing protection is critical:
- Prevents Unauthorized Access
Spoofing attacks often aim to bypass authentication systems and gain access to networks or sensitive information. Effective spoofing protection ensures that only legitimate users or devices can communicate with your systems, preventing unauthorized access.
- Protects Sensitive Information
Spoofing attacks like phishing and DNS spoofing are designed to trick users into sharing sensitive information, such as passwords, credit card numbers, or personal data. By preventing these attacks, spoofing protection safeguards confidential information from falling into the wrong hands.
- Maintains Network Integrity
In attacks like IP or ARP spoofing, cybercriminals can disrupt network traffic, intercept communications, or reroute data to malicious destinations. Spoofing protection helps maintain the integrity and reliability of networks by identifying and blocking malicious traffic.
- Prevents Financial Losses
Businesses targeted by spoofing attacks can suffer significant financial damage, whether through direct theft, loss of customer trust, or regulatory penalties. Anti-spoofing measures help mitigate these risks by ensuring that data and communications are secure.
- Protects Reputation
A spoofing attack, especially one that leads to data breaches or phishing scams, can damage a business’s reputation. Effective spoofing protection not only safeguards data but also helps maintain customer trust and brand reputation by preventing attacks.
- Complies with Security Regulations
Many industries require businesses to implement security measures that protect against spoofing and other cyber threats. Anti-spoofing technologies help organizations comply with regulatory standards, avoiding penalties and legal issues.
Challenges in Anti-Spoofing Technology
| Challenge | Description |
|---|---|
| Sophistication of Spoofing Techniques | Attackers continually evolve methods, making it hard for anti-spoofing technologies to keep up. |
| False Positives | Legitimate traffic or communications can be blocked by mistake, disrupting operations |
| Complexity in Deployment | Deployment of anti-spoofing systems can be complex, especially in large or outdated networks. |
| Lack of Standardization | Not all systems support the same standards, limiting the effectiveness of anti-spoofing measures. |
| Resource Intensity | Anti-spoofing systems require significant resources, which can be challenging for smaller organizations. |
| Biometric Spoofing Countermeasures | Sophisticated fake biometrics, like deepfakes, are hard for current systems to detect. |
| User Resistance and Inconvenience | Complex authentication measures may inconvenience users, leading to poor adoption. |
| Scaling Challenges | Anti-spoofing solutions may not scale well in large, distributed environments. |
| Increased Attacker Evasion Techniques | Attackers use techniques like encryption or DNS cache manipulation to evade detection. |
| Ongoing Maintenance and Updates | Anti-spoofing technologies require regular updates to remain effective against new threats. |