How can we be sure that the person accessing sensitive data is truly who they claim to be? Traditional biometric systems, like fingerprint and facial recognition, face increasing threats from sophisticated spoofing attacks using photos, videos, or replicas. Here liveness detection comes to the rescue. It is a cutting-edge technology designed to distinguish between a live person and a fake biometric sample.
This sophisticated system enhances security by analyzing subtle cues and behaviors that are impossible to replicate with static images or models. But how exactly does liveness detection work, and why is it so vital for modern security? Let's explore the intricacies of this essential technology.
Key Takeaways
- Liveness detection is a critical security measure used in biometric systems to verify that the biometric sample being presented is from a live person, preventing fraud and unauthorized access.
- There are two main types of liveness detection: active, which requires user interaction like blinking or smiling, and passive, which analyzes biometric samples without user involvement using advanced algorithms and sensors.
- Liveness detection relies on a combination of AI, machine learning, and specialized sensors such as infrared cameras and 3D depth sensors to analyze biometric samples for signs of life, such as micro-movements and light reflections.
- Liveness detection is used in various sectors, including financial services, mobile devices, access control, healthcare, government services, and e-commerce, enhancing security and preventing fraud.
- Key challenges include balancing accuracy to minimize false positives and negatives, ensuring a smooth user experience, managing costs and complexity, adapting to new spoofing techniques, integrating with existing systems, addressing privacy concerns, and mitigating the impact of environmental factors.
What is Liveness Detection?
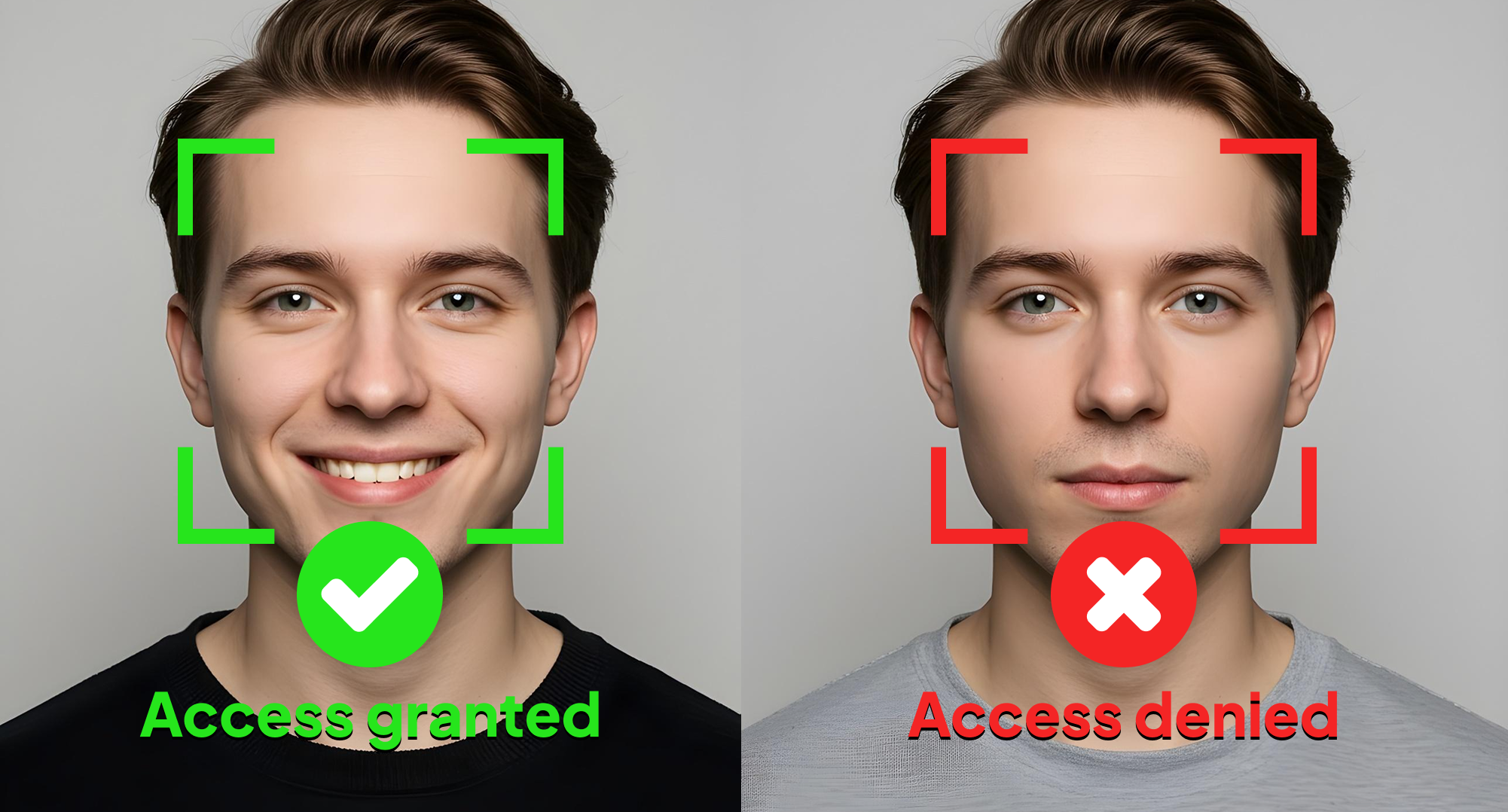
Liveness detection is an important security feature used in biometric systems to make sure the biometric sample being used comes from a live person, not a fake or copied one. This means that when you scan a fingerprint, face, or other biometric trait, the system checks to ensure it’s from a real person, not a photo, video, or replica. Liveness detection uses different methods to tell the difference, such as looking for changes in skin texture, eye movement, or small facial expressions. Adding this extra step helps prevent fake attempts to gain unauthorized access, making sure the biometric data is genuine and secure. This is especially important in high-security situations, where allowing a fake entry could cause serious problems.
Types of Liveness Detection
Liveness detection is classified into two main types: active and passive. Each type employs different techniques to verify the liveness of a biometric sample. Here’s an in-depth look at both:
Active Liveness Detection
Active liveness detection requires the user to perform specific actions, such as blinking, smiling, or moving their head, to prove their aliveness. These actions are monitored and analyzed by the system to confirm the presence of a live person. Here are some of the active liveness detection examples:
- Facial recognition systems: Users might be asked to blink, smile, or turn their heads to prove they are live. For instance, a smartphone unlocking system might prompt the user to blink their eyes, ensuring that the face being scanned is not a photograph or video.

- Fingerprint scanners: Some advanced fingerprint systems require users to apply varying pressure or move their finger in a particular way while scanning. This can help differentiate between a live finger and a fake mold or print.

- Voice recognition: Systems might ask users to repeat a random phrase or series of numbers to verify that the voice being recognized is not a recording.
Benefits
- High accuracy in detecting spoof attempts.
- Enhanced security due to user interaction.
Challenges
- Potential inconvenience for users due to required actions.
- Not always feasible in all situations (e.g., physical limitations).
Passive Liveness Detection
Passive liveness detection operates without any explicit action from the user. It relies on advanced algorithms and sensors to analyze the biometric sample for natural human traits, such as skin texture, subtle movements, and light reflection patterns, to determine liveness. Let’s explore some examples below.
- Facial texture analysis: This technique involves analyzing the texture and micro-movements of the skin. Advanced cameras capture detailed images of the face, and algorithms assess these images to detect natural, subtle movements that indicate liveness.
- Light reflection: Specialized sensors use light patterns and reflections to distinguish between a live face and a photograph or mask. For example, the way light reflects off a real face differs from how it reflects off a flat photo or a 3D-printed mask.
- 3D depth sensing: Using depth-sensing cameras, systems can capture a three-dimensional map of the face. This technology can detect the depth and contours of a live face, which cannot be replicated by 2D images or most masks.
Benefits
- No user interaction is required, providing a seamless experience.
- Can be integrated into various devices and applications without significant changes to user behavior.
Challenges
- May require more sophisticated hardware and algorithms.
- Balancing accuracy and false rejection rates can be complex.
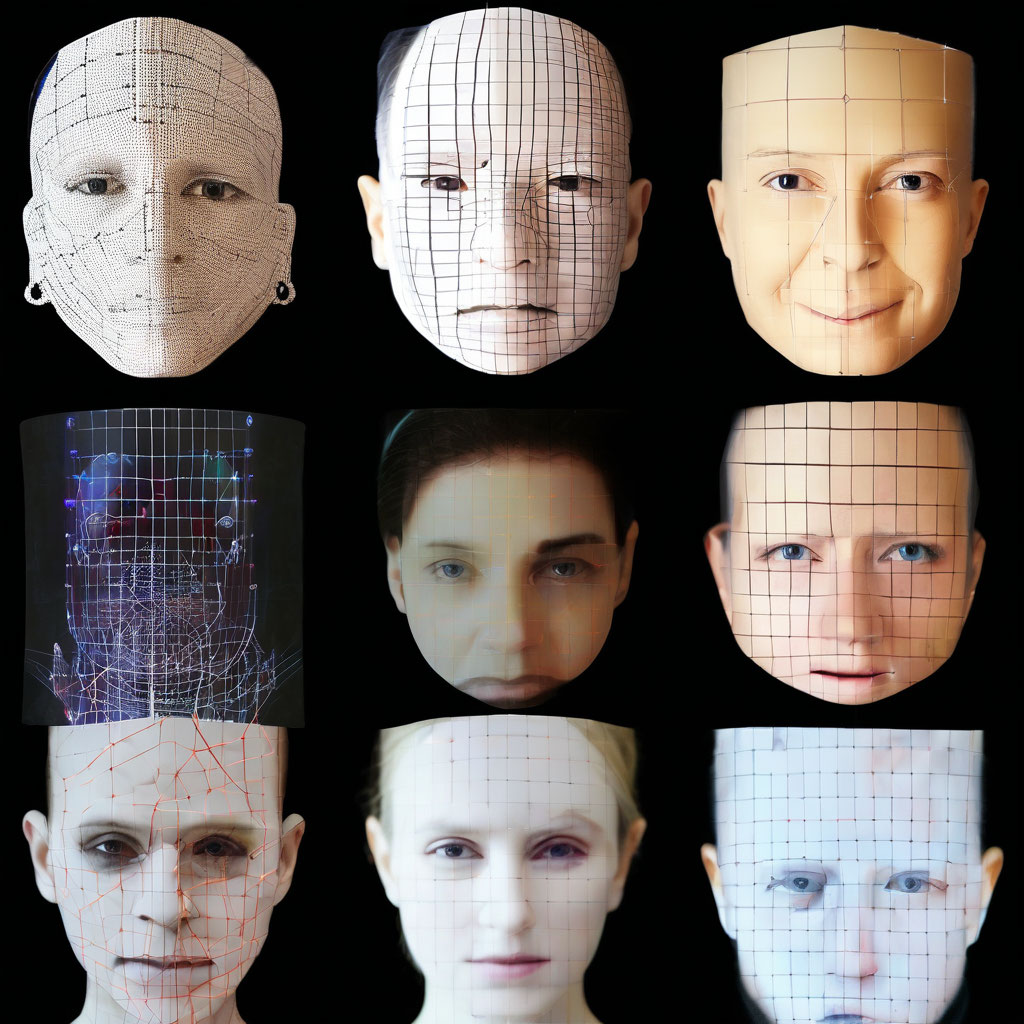
Image Data Collection for Biometric System
- Biometrics, Facial Identification
- 2,000 photographs across 50 unique sets
- 1 month
Why is Liveness Detection Important?
With the current volume of digital security breaches, liveness detection plays a crucial role in safeguarding sensitive information and systems. According to a report by Juniper Research, the spending on digital identity verification checks will reach $20.8 billion globally in 2027. Here’s why liveness detection is essential:
Preventing Identity Fraud
One of the primary reasons for implementing liveness detection is to prevent identity fraud. Traditional biometric systems can be tricked using photos, videos, or replicas. Liveness detection ensures that the biometric sample being presented is from a live person, making it significantly harder for fraudsters to gain unauthorized access.
Examples:
- Financial services: In online banking, liveness detection ensures that the person conducting a transaction is the legitimate account holder, not someone using a stolen photo or video.
- E-commerce: During online purchases, liveness detection can prevent fraudsters from using stolen biometric data to make unauthorized transactions.
Enhancing the Security of Mobile Devices
Mobile devices are frequently used for personal and professional tasks, making them prime targets for cyber-attacks. Liveness detection enhances the security of mobile devices by ensuring that only the device owner can unlock and access the device.
Examples:
- Smartphones: Modern smartphones use facial recognition or fingerprint sensors to unlock the device. Liveness detection adds an extra layer of security by verifying that the biometric sample is from a live person.
- Tablets: Similar to smartphones, tablets with biometric authentication features benefit from liveness detection to prevent unauthorized access.
Securing Physical Access
Liveness detection is also vital for securing physical access to sensitive areas. It ensures that only authorized individuals can enter restricted locations, enhancing overall security.
Examples:
- Data centers: High-security areas like data centers require stringent access controls. Liveness detection prevents unauthorized individuals from gaining access using fake biometric samples.
- Corporate offices: In corporate environments, liveness detection ensures that only employees can enter secure areas, protecting sensitive information and assets.

Reducing False Acceptance Rates
Biometric systems without liveness detection are prone to false acceptance rates, where unauthorized individuals gain access using fake biometric samples. Liveness detection significantly reduces these rates, ensuring that only genuine biometric samples are accepted.
Examples:
- Access control systems: In buildings and facilities with biometric access control, liveness detection ensures that only authorized personnel can enter, reducing the risk of false acceptance.
- Automated Teller Machines (ATMs): ATMs equipped with liveness detection can prevent unauthorized individuals from accessing bank accounts using fake fingerprints or facial images.
Building User Trust
Implementing liveness detection in biometric systems helps build user trust by providing a secure and reliable authentication process. Users are more likely to trust and use biometric systems if they know their data is protected against spoofing attempts.
Examples:
- Healthcare systems: Patients are more likely to trust digital health records and telemedicine services if they know that their biometric data is protected by liveness detection.
- Government services: Citizens are more likely to engage with e-government services if their biometric data is securely protected against fraudulent use.
How Does Liveness Detection Work?
Liveness detection operates through a combination of advanced technologies and sophisticated algorithms designed to differentiate between live biometric samples and spoofed attempts. Here’s a detailed look at how liveness detection functions:
Technological Foundation
Liveness detection systems rely on a mix of hardware and software to accurately determine whether a biometric sample is from a live person.
Algorithms and AI
Advanced artificial intelligence (AI) and machine learning algorithms play a crucial role in analyzing biometric samples. These algorithms are trained to recognize the subtle differences between live and fake samples by examining various features such as texture, movement, and light reflection.
Sensors
Specialized sensors, including infrared cameras, 3D depth sensors, and light sensors, are employed to capture detailed biometric data. These sensors provide the necessary input for algorithms to analyze and verify liveness.
Process Breakdown
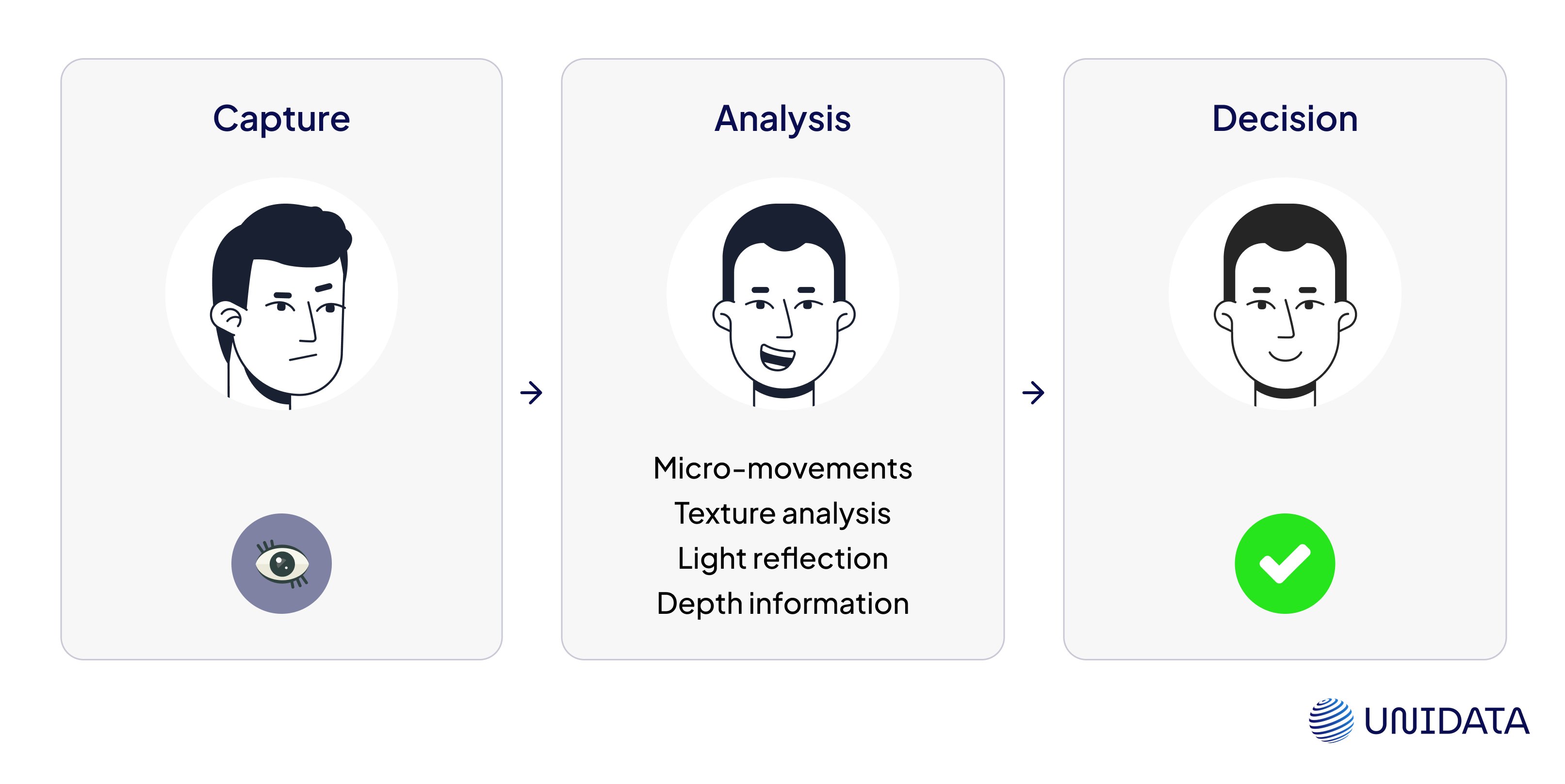
The liveness detection process typically involves three key stages: capture, analysis, and decision.
- Capture
The system captures the biometric sample, such as a fingerprint, facial scan, or iris scan, using high-resolution cameras or sensors. This initial step is crucial for obtaining a detailed and accurate representation of the biometric trait.
- Analysis
Once the biometric sample is captured, the system analyzes it for signs of liveness. This analysis includes several techniques:
- Micro-movements: The system checks for natural, involuntary movements such as slight facial twitches or the pulsation of blood vessels in the finger.
- Texture analysis: Advanced algorithms examine the texture of the skin, looking for natural skin patterns and inconsistencies that are hard to replicate with fake samples.
- Light reflection: The way light reflects off a live face or finger differs from how it reflects off a photo, mask, or mold. The system analyzes these light patterns to determine authenticity.
- Depth information: Using 3D depth sensors, the system captures a three-dimensional map of the face or finger. This depth of information helps distinguish a live sample from a flat image or replica.
- Decision
Based on the analysis, the system makes a decision on whether the biometric sample is from a live person or a spoof attempt. If the sample passes the liveness check, access is granted; otherwise, it is denied.
What Is Object Detection in Computer Vision?
Learn more
Liveness Detection Applications
Liveness detection technology is increasingly being integrated into various systems and industries to enhance security and ensure the authenticity of biometric data. Here are some key applications of liveness detection:
Preventing Fraud in Financial Services
Liveness detection is critical in the financial sector to prevent fraud and unauthorized transactions. It ensures that only the account holder can access their banking services, whether online or at ATMs.
Examples:
- Online banking: When customers log in to their online banking accounts using facial or fingerprint recognition, liveness detection verifies that the biometric data is from a live person.
- ATMs: ATMs equipped with biometric scanners use liveness detection to ensure that the fingerprint or face being scanned belongs to a live individual, preventing access to fake fingerprints or photos.
Enhancing Security in Mobile Devices
Smartphones and tablets, often used for banking and personal data access, are key targets for cyber-attacks. Liveness detection adds a powerful security layer to biometric features like face and fingerprint recognition.
Examples:
- Devices such as iPhones and Android smartphones use liveness detection in Face ID or fingerprint unlock systems to verify the presence of a real user.
- Mobile payment apps like Apple Pay or Google Pay rely on biometric checks that include liveness detection to prevent unauthorized purchases.
According to a study by iProov, 80% of users either prefer or are comfortable with online face verification, highlighting strong public support and trust in liveness detection as a secure method for identity verification.
Securing Physical Locations
Liveness detection is vital for securing physical access to sensitive areas, ensuring that only authorized individuals can enter.
Examples:
- Corporate offices: Biometric access control systems in corporate environments use liveness detection to verify that only employees can access restricted areas, protecting sensitive data and assets.
- Data centers: High-security areas like data centers employ liveness detection to prevent unauthorized individuals from gaining access using fake biometric samples.
Protecting Patient Data
In the healthcare sector, protecting patient data is paramount. Liveness detection helps secure access to electronic health records (EHRs) and other sensitive information.
Examples:
- Electronic health records: Healthcare providers use liveness detection to ensure that only authorized personnel can access patient records, preventing unauthorized access and data breaches.
- Telemedicine: During virtual consultations, liveness detection ensures that the person accessing the service is indeed the patient, maintaining the confidentiality and integrity of medical interactions.
Healthcare remains the most expensive industry for responding to and recovering from data breaches, a rank the sector has held since 2011, according to a report by IBM and the Ponemon Institute.
Ensuring Secure Access in Government Services
Government services increasingly rely on biometric authentication for secure access to services and information. Liveness detection enhances the security and trustworthiness of these systems.
Examples:
- e-Government services: Citizens accessing government services online use biometric authentication with liveness detection to ensure secure and legitimate access.
- Border control: At border crossings, biometric systems with liveness detection verify travelers' identities, enhancing security and preventing illegal entry using fake documents or biometric data.
Securing Transactions in E-commerce
In e-commerce, ensuring the authenticity of users is crucial for secure transactions. Liveness detection helps prevent fraudulent activities during online shopping and payments.
Examples:
- Online shopping: When making purchases, liveness detection ensures that the person making the payment is the legitimate account holder, reducing the risk of fraud.
- Digital wallets: Biometric authentication with liveness detection secures digital wallets, ensuring that only the rightful owner can access and use the funds.
Challenges of Liveness Detection
While liveness detection significantly enhances biometric security, it faces several challenges that can impact its effectiveness and implementation. Here are some of the primary challenges.
| Challenge Area | Description |
|---|---|
| False positives and false negatives | Balancing accuracy: One of the most significant challenges is balancing the accuracy of liveness detection systems to minimize false positives (accepting a fake biometric as real) and false negatives (rejecting a real biometric as fake). Both types of errors can have serious consequences, from unauthorized access to legitimate users being denied access |
| User experience | Convenience vs. security: Ensuring a smooth user experience while maintaining high security is a delicate balance. Active liveness detection methods, which require user interaction, can sometimes be intrusive and inconvenient. Conversely, passive methods, although less intrusive, need to be highly accurate to avoid frustrating users with false rejections |
| Cost and complexity | Implementation costs: Implementing liveness detection often involves significant costs, especially for advanced sensors and sophisticated algorithms. This includes the expense of purchasing high-quality hardware and the ongoing costs of developing and maintaining complex software systems |
| Technological limitations | Adapting to new spoofing techniques: As spoofing techniques become more sophisticated, liveness detection systems must continuously evolve to counter these threats effectively. This requires constant innovation and adaptation to stay ahead of malicious actors |
| Integration and compatibility | System integration: Integrating liveness detection with existing biometric systems and ensuring compatibility across different devices and platforms can be complex. Older systems may not support the advanced sensors or algorithms required for effective liveness detection, and ensuring consistent performance across various environments is challenging |
| Privacy concerns | Data security: Collecting and storing detailed biometric data for liveness detection raises privacy concerns. Ensuring that this data is protected against breaches is crucial, and systems must comply with data protection regulations, which can vary by region and impose strict requirements on data handling |
| Environmental factors | External influences: Environmental factors such as lighting conditions, background noise, and user position can impact the accuracy and reliability of liveness detection systems. Poor lighting can affect facial recognition, and background noise can interfere with voice recognition, making it challenging to maintain consistent performance |
Summary
Liveness detection is a vital component of modern biometric security systems, ensuring that biometric samples come from live individuals and not from spoof attempts. By utilizing advanced technologies like AI, machine learning, and specialized sensors, liveness detection significantly enhances security across various applications, from financial services and mobile devices to healthcare and government services.
Despite challenges such as balancing accuracy, user experience, and cost, ongoing advancements are making liveness detection more reliable and accessible. As digital threats continue to evolve, the importance of robust liveness detection systems will only grow, protecting sensitive information and ensuring secure access.